The very best of the of B-sides
Category: arete
The Art of Cyberwar | Part VI | Weak Points and Strong

The principle:
“So in war, the way is to avoid what is strong and to strike at what is weak.”
Strength and Weakness Are Temporary
Sun Tzu emphasized that strength and weakness are dynamic rather than static. Although this principle may seem self-evident, it is often overlooked in practice. Many individuals disregard straightforward strategies, mistakenly believing that complexity is required. This oversight often leads to the violation of previous strategic principles or “lessons learned”, indicating a lack of genuine understanding.
It is essential to recognize that what appears robust today may become fragile in the future, while seemingly vulnerable elements can become decisive with time and increased awareness.
Power, whether military or digital, shifts with context.
The critical factor is not the quantity of resources, but the ability to perceive the entire operational landscape. Vulnerabilities arise not only from an adversary’s strengths, but also from areas where situational awareness is lacking and the speed at which adaptation occurs when new realities emerge.
In contemporary contexts, both nations and security architects often neglect this fundamental principle. There is a tendency to focus on constructing increasingly formidable defenses rather than developing adaptive strategies. Regardless of the scale of these defenses, adversaries require only minor vulnerabilities to compromise their effectiveness. Always remember, your adversaries only need to find a tiny leak in the walls to bring the entire system down.
Predictability: The Modern Weakness
Even the most secure fortresses eventually become familiar terrain for attackers. Cyber adversaries do not rely on brute force; instead, they employ strategic analysis. They examine organizational habits and exploit vulnerabilities such as unpatched servers, unmanaged privileged or service accounts, unchanged passwords, and the susceptibility of executives to social engineering.
Their success depends not on force, but on the predictability of organizational behaviors.
Nations exhibit similar vulnerabilities. Bureaucratic routines solidify into doctrine, which can devolve into dogma. Adversaries exploit these predictable patterns, waiting for repetition before executing successful attacks.
Historical events, such as the Pearl Harbor attack, the September 11 attacks, the Gulf of Tonkin incident, and numerous cyber intrusions, demonstrate that deficiencies in critical thinking, complacency, rigidity, and hubris significantly increase the likelihood of successful surprise attacks.
When Comfort Masquerades as Strength
Many organizations and governments allocate excessive resources to familiar areas, fostering a false sense of security. This environment allows risks to proliferate unnoticed, undermining overall resilience.
Cybersecurity teams often spend millions fortifying infrastructure while leaving users untrained.
Organizations frequently monitor technical metrics while neglecting human behavior. The most significant vulnerabilities often arise from areas presumed to be under adequate management.
System failures are typically attributable not to insufficient funding, but to misaligned priorities.
This pattern is evident at the national level as well. Large militaries and substantial budgets often obscure underlying fragilities, including slow adaptation, reliance on outdated assumptions, unstable alliances, and insufficient strategic foresight regarding emerging forms of conflict.
Historical Lessons of Misguided Strength
The First World War began with nations convinced that industrial might and rigid plans guaranteed victory. Those plans dissolved within months under the weight of modern weapons and static thinking.
During the Vietnam War, a major power misinterpreted its capacity for endurance as a guarantee of superiority. The Viet Cong’s guerrilla tactics transformed conventional advantages into significant liabilities.
Even the rapid success of Operation Desert Storm fostered complacency. Efficiency was mistaken for enduring security, and the perceived triumph was erroneously interpreted as evidence of invincibility.
Each era reaffirms the principle that the most conspicuous assets are not necessarily the most powerful.
Flexibility as True Power
Sun Tzu’s insight was to conceptualize power as dynamic movement. He advocated that a general should emulate water, seeking the path of least resistance and adapting to the terrain.
Within the cyber domain, the operational landscape evolves rapidly, with new threats, actors, and vulnerabilities emerging on a continual basis.
In this context, strength is defined by agility:
- Rotate keys and credentials regularly.
- Automate but verify.
- Decentralize authority so teams can act without waiting for hierarchy.
The most effective defenders are those who demonstrate the greatest adaptability, learning and evolving more rapidly than adversaries can adjust their tactics.
Lao Tzu’s Echo
Lao Tzu put it simply:
“Water overcomes the stone not by strength, but by persistence.”
Endurance surpasses dominance. Properly understood, flexibility is not a sign of weakness but of resilience, characterized by the capacity to absorb disruption and recover to an original state.
In the digital context, resilience is reflected in recovery planning, redundancy, and organizational culture. The true measure of strength is not the infrequency of failure, but the speed of recovery following a compromise.
Turning Weakness Into Insight
All systems possess inherent flaws. Denial of these vulnerabilities allows them to remain concealed until a crisis occurs. Proactive defenders employ audits, red-team exercises, and transparent communication to identify weaknesses at an early stage.
Transparency transforms potential liabilities into opportunities for organizational learning.
Nations could use the same humility.
Public acknowledgment of mistakes enhances credibility, whereas concealment increases risk. The most resilient governments are not those without flaws, but those capable of adapting transparently before their constituents.
From Awareness to Action
Identifying vulnerabilities constitutes only part of the challenge; addressing them effectively demands both discipline and restraint.
In cybersecurity, this approach entails prioritizing remediation over self-congratulation, thorough preparation prior to disclosure, and critical evaluation before taking action.
In policy contexts, this requires deliberate prioritization, engaging only in actions where the anticipated outcomes justify the associated costs.
Misapplied strength can become a source of vulnerability, whereas a thorough understanding of weaknesses can provide strategic foresight.
The Next Step: The Flow of Force
Sun Tzu ends this chapter with motion: the strong shifting to the weak, the weak transforming to the strong.
He implies that awareness must evolve into timing. The wise general aligns his force with the moment, not against it. And that, “All men can see the tactics whereby I conquer, but what none can see is the strategy out of which victory is evolved.”
This concept serves as a transition to the subsequent lesson, which focuses on the dynamics of energy in motion and the strategic management of power with balance and rhythm.
We’ve learned where to stand. Next, we’ll learn how to move. As Master Tzu concludes Chapter VI:
Military tactics are like unto water; for water in its natural course runs away from high places and hastens downwards. Water shapes its course according to the nature of the ground over which it flows; the soldier works out his victory in relation to the foe whom he is facing. Therefore, just as water retains no constant shape, so in warfare there are no constant conditions.
Leading us directly back to this lesson’s seemingly simple principle: “So in war, the way is to avoid what is strong and to strike at what is weak.”
Feast Like a Pro: Gratitude, Gains & Turkey Day Tactics

The table is set. The family is gathered. That golden bird’s resting for its moment of glory. And you? You’re not just another guest, you’re the standard‑bearer. Training hard doesn’t hibernate because of a holiday. Neither does integrity, nor does your plate.
If you’ve spent years training in the trenches, on the mats, under the barbell, through years of high-demand cycles, you know one thing: what you do in ordinary weeks sets up your success in the extraordinary ones. Thanksgiving falls in the extraordinary category, but it doesn’t need to wreck your rhythm. It can elevate it.
Why Thanksgiving can work to your advantage
Many of those holiday staples are good food choices: turkey provides lean protein, sweet potatoes offer fiber and micronutrients, and greens contribute volume and nutrient density.
The catch isn’t the food, it’s the habits before and after that singular day that matter far more.
Let’s keep the feast, skip the fallout.

Three rules to guide you at the table
- Start Strong
Don’t arrive famished. Your engine shouldn’t be at the red‑line before the first bite. A balanced breakfast, eggs and veggies, cottage cheese and berries, or Greek yogurt and nuts, all keep hunger in check and your nervous system grounded. Research confirms that skipping breakfast often triggers overeating and leaves you feeling exhausted. - Always Balance Your Plate
Picture any other day’s nutrition: lean protein to anchor (such as turkey, beef, or ham), colorful vegetables or salad for volume, and limited starchy sides unless your training week demands them. Watch the gravy and sauces, those are where the hidden (and delicious) calories hide. - Mind the Velocity
Feasting is a moment. Not a month. At the end of the meal, don’t fear choosing to eat something you love: pie, sides, or other family favorites. But just enjoy semi-reasonable portions. Experts show that a single large meal won’t derail you long‑term. So, don’t live in fear of enjoying yourself. Your habits of hard training and clean eating will remain just as they were the day before Thanksgiving. Finish the meal with water, a walk, or even a short mobility circuit. Movement after eating boosts digestion and circulation, and helps you avoid the all‑too‑familiar food coma. But don’t be weird about it!
A bit of real-life experience:
I’ve seen high-level athletes treat Turkey Day like a dead zone. They think “holiday = derail.” Instead, I coach it like any other session: first of all, your habits and discipline got you here. After that, it’s just preparation, execution, and recovery. You arrive with your baseline, you feast with intention, you leave the table with your standards intact. That same mindset built you under the barbell and in the academy; it works here, too.
This week’s actionable plan
- Open your day with intention: Have a solid breakfast, something you’d have on a heavy training day.
- Scan the table before loading your plate: protein first, then vegetables, and then one or two sides you love.
- Pick one indulgence: It’s OK. But make it a choice, not a subconscious default.
- Finish strong with movement: a 15–20 minute walk, foam roll, or light mobility work post-meal. But again, don’t be weird about it. Don’t be “that guy.”
- Back to normal tomorrow: One meal doesn’t define you. Your pattern does.
Ultimately, it isn’t about perfection. It’s about being present with your family and friends. Celebrating with those you care about, giving thanks, and still showing up for your future self, too.
Training, eating, and living at a high level don’t pause for holidays; they simply work in harmony with them.
The Art of Cyberwar, Part V | Energy | The Use of Force

The principles:
In all fighting, the direct method may be used for joining battle, but indirect methods will be needed in order to secure victory.
Indirect tactics, efficiently applied, are inexhaustible as Heaven and Earth, unending as the flow of rivers and streams; like the sun and moon, they end only to begin anew; like the four seasons, they pass away to return once more.
The Power of Controlled Motion
Sun Tzu’s fifth chapter deals with energy, not as brute strength, but as direct application of force.
He warned that a commander must know when to cultivate and store power and when to release it. Misapplied use of Energy burns itself out. However, when energy is focused, it bends the world to its will.
It’s an idea that translates effortlessly to today’s digital battlefield. Nations, like networks, often fail not because of a lack of capability, but because of a lack of control.
True mastery isn’t in how much force you can deploy. It’s in knowing how little you need to. It’s akin to the idea that, sure, you can kill a fly with a hammer, but is it the most effective tool at your disposal?
The Cost of Unchecked Energy
American Diplomatic and Military History is full of examples of lawmakers mistaking our capacity for clarity.
In Korea, overwhelming U.S. power pushed back North Korean forces, only to overextend toward China’s border and trigger an entirely new front. And thus, we have burdened ourselves with maintaining the “38th parallel” ever since.
In Vietnam, energy became inertia, force applied endlessly without definition, draining political and moral capital alike. If only the “peacemakers” at the Treaty of Versailles had let Ho Chi Minh deliver his speech on the Rights of Man, perhaps there would have been no quagmire in Southeast Asia to begin with. A guerrilla war that would take nearly 60,000 American lives and lead to what became known as the “Vietnam Syndrome.”
In Iraq, “shock and awe” demonstrated that a singular “tactical victory” can be swift, while a strategic victory remains elusive. Notwithstanding the entire list of false pretenses that led to the invasion of Iraq to begin with.
Each conflict began with a belief in momentum and ended with war fatigue. Demonstrating once again, force without direction always collapses under its own weight.
The lesson isn’t that force is wrong; it’s that force, when misapplied and unguided, becomes self-consuming. Power is not infinite. Neither is attention, money, or public trust.
The Cyber Equivalent: Sprawl and Burnout
Organizations repeat these same mistakes in digital form.
A breach occurs, and the reflex is to rush to acquire new tools, policies, and budgets, thereby triggering a cyberwar “surge.”
New dashboards, new alert monitoring, and new vendors lead to a surge in activity, while clarity plummets.
This is cyber energy without strategy, effort disconnected from insight.
As Sun Tzu also said: Amid the turmoil and tumult of battle, there may be seeming disorder and yet no real disorder at all; amid confusion and chaos, your array may be without head or tail, yet it will be proof against defeat.
Teams exhaust themselves chasing incidents instead of patterns. Leaders demand constant escalation, not realizing that perpetual crisis is its own vulnerability.
The result mirrors the national trap: motion is mistaken for genuine progress. The ability to endure is mistaken for endurance.
Energy as Rhythm, Not Frenzy
Sun Tzu described two forms of force:
- Normal energy — the steady discipline that sustains the fight.
- Extraordinary energy — the precise, unexpected burst that wins it.
In cybersecurity, the equivalent is security posture and precision in the application of policies.
Normal energy is the quiet work of patching, monitoring, and awareness training. Extraordinary energy is the calm, swift, and accurate incident response that turns chaos into closure.
Both are needed. But one cannot exist without the other. A team that never rests has no energy left to strike when it matters most.
It’s the same in martial arts.
In Wing Chun:
Normal energy = quality structure and energy sensitivity.
Extraordinary energy = the skill to deliver a singular, intercepting strike that ends the exchange.
Muay Thai:
Normal energy = footwork, guard, pacing.
Extraordinary energy = the slashing elbow, a stabbing teep, or perfectly placed knee.
BJJ:
Normal training energy = position, pressure, framing.
Extraordinary training energy = the ability to feel a submission triggered by feeling the opponent’s mistake. Or in Mandarin it’s an old idea called Wu Wei, or effortless action. Meaning, I don’t present the opportunity to attack; the enemy presents it to me, like water finding a leak in the dam.
A Security Team that never rests has no energy left for anything extraordinary.
Good CISOs, like good generals, good fighters, and good grapplers, understand rhythm. They know when to conserve strength so that action, when it comes, is clean and effective.
As Master Tzu also knew, “When he utilises combined energy, his fighting men become as it were like unto rolling logs or stones.” Leading to, … “the energy developed by good fighting men is as the momentum of a round stone rolled down a mountain thousands of feet in height. So important is the subject of energy.”
Diplomacy and the Misuse of Force
In diplomacy, the same physics apply. The U.S. has often wielded immense power but uneven patience.
Moments like the Marshall Plan and the Cuban Missile Crisis demonstrated the value of precision, employing limited force, clear objectives, and a proportional response.
But elsewhere, the misapplication of force became diplomatic impotence on full display. Prolonged occupations and open-ended interventions constantly drain strategic reserves of will and trust.
Every drone strike, every unconstitutional data collection program, every new cyber warfare doctrine carries a similar risk: that power’s convenience will overshadow its consequence.
The Taoist counterpoint from Lao Tzu still resonates to this day:
“He who knows when to stop never finds himself in trouble.”
Knowing when not to act is the highest use of force. It’s the difference between control and compulsion.
The Lesson for Cyber Strategy
A strong digital defense isn’t constant action, it’s intelligent action.
Practical translation:
- Automate the repeatable.
- Escalate only with context.
- Protect attention as aggressively as data.
- Reserve extraordinary effort for extraordinary situations.
Energy mismanaged becomes sprawl. Energy focused becomes resilience.
It’s never the size of the arsenal. It’s the precision of the response.
Momentum and the Myth of Constant Action
Modern life rewards constant motion, refresh, respond, and reply.
In cybersecurity and foreign policy alike, stillness feels dangerous to the untrained mind.
But strategy lives in the pause between movements. Quality fighting skills are always more effective when you can strike on the half-beat, a fundamental separator on the mats, and on digital and physical battlefields.
Force has a short half-life. When it’s used endlessly, it decays quickly and fades into the ether. When it’s reserved for the right moment, it changes everything.
A breach contained quietly is often a bigger victory than a public takedown.
A crisis de-escalated without violence often preserves more stability than any show of strength.
Knowing When to “Flow With the Go”
As one of the greatest living legends in Brazilian Jiu-Jitsu, Rickson Gracie once said, “In Jiu Jitsu we flow with the go.”
Meaning:
- don’t fight force with tension
- stay aware but not trapped by focus
- stay smooth and adaptive
- flow with the opponent’s energy
- let well-trained instinct and structure guide you
That metaphor fits the digital era perfectly. The best blue or purple teamers, like the best leaders, don’t fight the current; they learn to read it and swim with it, not against it.
Lao Tzu would say that “the soft overcomes the hard,” not through weakness but adaptability. Force channeled through awareness is stronger than force spent in anger.
In warfare and cybersecurity alike, energy is a currency. Spend it recklessly and you’ll be empty when it matters. Spend it wisely and you’ll be leading on the battlefield.
Final Reflection
Knowing how to use force is knowing its limits.
Sun Tzu and Lao Tzu shared the same truth from opposite angles:
Power must be balanced by patience.
Energy must be stored as much as it is spent.
History punishes those who forget this. So does network and security architecture.
The art isn’t in using force; it’s in knowing when the situation calls for little, none, or overwhelming force.
That’s not mysticism. That’s strategic maintenance. And it’s as accurate in security architecture as it is on the battlefield.
All of these lessons point us directly back to our opening principles: “In all fighting, the direct method may be used for joining battle, but indirect methods will be needed to secure victory.” And, “Indirect tactics, efficiently applied, are inexhaustible as Heaven and Earth, unending as the flow of rivers and streams; like the sun and moon, they end only to begin anew; like the four seasons, they pass away to return once more.
The wise strategist learns to move the same way.
Fuel to Perform: The Athlete’s Edge in Everyday Eating
If you show up on the mats, under the barbell, or work hard to refine your gymnastic skills with any kind of serious intent, you’re not just training. You’re preparing and refining, often asking your body to do more than the day before. In our world, what you eat becomes the difference between a “good session” and a “great session,” and between strategic recovery and systemic breakdown. It’s the small details that separate showing up from showing out!

Let’s skip the noise and get tactical: how do semi-competitive athletes or serious recreational competitors fuel performance when life’s messy—work, travel, kids, and tired mornings? Let’s make it real.
The Big Picture
Research shows nutrient timing matters, especially around workouts. The ISSN says, “Purposeful ingestion of nutrients at various times throughout the day” (source) supports strength, power, body composition, and performance.
But for your average serious athlete? The “anabolic window” isn’t a specific, narrow window where you must cram in a meal. That “window” is basically as wide as a garage door. You don’t need perfect timing; it’s about being prepared at the right time.
Three Fuel Strategies That Work
1. Pre-training Anchor Meal
Eat something 60-90 minutes before your session: a moderate amount of carbs, lean protein, and a lighter amount of fat. Example: oatmeal with banana + a scoop of whey or Greek yogurt. Why? You’re topping off glycogen and priming your engine. If you train early and can’t eat, choose a liquid option: an easy-to-digest protein and carb-balanced smoothie.
2. In Training Mini Feeding (When It’s Longer or More Intense)
If your session lasts more than 60 minutes or you’re doing back-to-back days, plan a quick carb hit mid-session (30–60g) and hydrate thoroughly. Why? To prevent an energy crash during your training and help protect your neurologic control.
3. Post Training Recovery Meal
Hit carbs + protein within 1–2 hours after intense work. Aim for a carb-to-protein ratio of roughly 3:1 to 4:1. Why? To replenish muscle glycogen, repair muscle, and prepare for your next session. Example: 4-6oz chicken breast, 1/2 sweet potato, 1 cup of roasted veggies drizzled with garlic-infused olive oil + 1 banana + 1 tbsp peanut butter.
How to adjust for workload (without going neurotic)
• Light day/skill day: Reduce carbs by ~20–30% and keep protein moderate.
• Heavy day/max effort session: Increase carbs by 10–20%, keep protein steady.
• Rest day: Keep protein consistent, reduce carbs/fats based on hunger, not fear.
You don’t need daily macro spreadsheets. Just know your baseline, use a fuel strategy, and build awareness. This gets easier each week and with every rep.

Notes from the Field
I’ve watched CrossFit athletes and tactical team members burn themselves out because they consistently skipped their pre-session carbs or failed to track and meet their protein intake for 2 or 3 consecutive days. When your training really matters, you have to treat eating like it’s a part-time job. I’ve run a meal prep business, coached fighters, been a fighter, and lived and trained overseas. I know that life because I’ve lived and breathed it for years. Fueling with purpose is fundamental.
Super Simple Action Steps You Can Take This Week
Pick one heavy training day and one rest/light day. Write down your usual food. For the heavy day, increase pre- and post-training carbs. On a rest day, maintain a steady protein intake and reduce carbohydrates by approximately 20%. Have a pre-workout anchor meal 60 minutes before a session. Note your energy, focus, and performance.
Log your post-training recovery meal within 2 hours after a session—get your carb and protein hit. Track how you feel the next day.
The key takeaways: Fuel consistently, match carbs to your workload, prioritize recovery, and make eating part of your training routine.
Train. Eat. Recover. Repeat.
If you’re training to lead from the front, fuel like someone already ahead of the pack.
The Art of Cyberwar | Part IV | Tactical Dispositions
The Principles:
“The good fighters of old first put themselves beyond the possibility of defeat, and then waited for an opportunity of defeating the enemy.”
“Thus it is that in war the victorious strategist only seeks battle after the victory has been secured, whereas he who is destined to be defeated, first fights, and afterwards looks for victory.” —Sun Tzu
Every data breach, foreign conflict, and policy error typically originates from an action taken without adequate prior positioning.
There is a common tendency to conflate activity with progress. Sun Tzu recognized that true invincibility is rooted in defense, while the opportunity for victory depends on the adversary.
In contemporary terms, this concept is referred to as defensive posture: the disciplined practice of preparation prior to visibility.
Defensive Positions
Effective cybersecurity teams secure their positions well in advance of any actual test. They maintain comprehensive awareness of data locations, access privileges, and the criticality of various systems. Such teams implement patches discreetly, monitor systems consistently, and design infrastructures to recover from failures rather than assuming failures will not occur.
That’s tactical disposition:
- Enforcing least privilege to build resilience.
- Applying timely patching to keep critical systems protected.
- Building backups as integrated mechanisms for redundancy and recovery.
- Running tabletop exercises to rehearse scenarios that organizations hope never occur.
This often-invisible work may appear inconsequential until it proves essential in critical moments.
When Nations Forget the Same Lesson
Historical evidence indicates that both nations and organizations seldom pause sufficiently to engage in strategic reflection.
Nations often amass extensive arsenals, initiate large-scale programs, and extend supply lines to project strength. However, when strength is dispersed excessively, it transforms into fragility, a phenomenon known as overreach. Overreach fundamentally undermines resilience.
The United States has frequently responded to perceived threats with disproportionate measures, conflating activity with effective strategy and reallocating resources without a long-term perspective. Engagements in wars and alliances often occur more rapidly than preparations for their potential consequences.
The consequences include wasted resources, public fatigue, and strategic exhaustion. All of which contribute to diminished geopolitical and geostrategic self-awareness.
According to Sun Tzu, achieving invincibility does not involve amassing weapons, engaging in unnecessary interventions, or imposing ineffective sanctions. Instead, it requires constructing economic, digital, and diplomatic systems capable of absorbing shocks while maintaining integrity. A resilient nation need not swing at every shadow.
Resource Stewardship
Cybersecurity is frequently perceived as a process of continual escalation, characterized by the addition of more tools, dashboards, and alerts.
However, each new platform introduces additional complexity, which in turn creates new potential attack surfaces.
Effective security practices may require declining adoption of the latest technologies and decommissioning unnecessary systems to simplify complex environments.
As Bruce Lee once said “I fear not the man who has practiced 10,000 kicks once, but I fear the man who has practiced one kick 10,000 times.”
Simplifying operations enables organizations to concentrate on mastering essential tools, particularly when resources are limited. The principles of simplicity, directness, and economy of motion are fundamental to effective practice.
Our government should also learn to exercise the same restraint. Faithful stewardship isn’t constant investment in everything; it’s a deliberate focus on what matters most.
This approach exemplifies strategic minimalism, which emphasizes the optimal utilization of public resources and, ultimately, enriches us all by conserving precious and limited resources.

Similarly, as America’s original Foreign Policy was initially articulated by John Quincy Adams on July 4th, 1821:
[America]…goes not abroad, in search of monsters to destroy. She is the well-wisher to the freedom and independence of all.
She is the champion and vindicator only of her own.
She will commend the general cause by the countenance of her voice, and the benignant sympathy of her example.
She well knows that by once enlisting under other banners than her own, were they even the banners of foreign independence,
She would involve herself beyond the power of extrication, in all the wars of interest and intrigue, of individual avarice, envy, and ambition, which assume the colors and usurp the standard of freedom.
The fundamental maxims of her policy would insensibly change from liberty to force…
She might become the dictatress of the world. She would be no longer the ruler of her own spirit…
[America’s] glory is not dominion, but liberty. Her march is the march of the mind. She has a spear and a shield: but the motto upon her shield is, Freedom, Independence, Peace. This has been her Declaration: this has been, as far as her necessary intercourse with the rest of mankind would permit, her practice.
This practical wisdom may appear boring. However, organizations and governments alike must identify their assets, maintain them, and protect only what can be effectively defended. Continuous review, revision, and updates are fundamental.
The Cost of Perpetual Readiness
Sun Tzu cautioned that armies maintained in the field for extended periods deplete their own strength. Contemporary parallels include budgets exhausted by perpetual emergencies and professionals experiencing burnout due to continuous false positives.
The solution lies in cultivating a well-developed security posture rather than succumbing to ongoing panic and overreaction.
Organizations should prepare comprehensively, rest intentionally, and engage only when strategically necessary.
This sequence, prioritizing defense before offense and clarity before action, establishes the resilience that many organizations seek.
Learning From Tactical Blindness
Security breaches frequently result from overlooked fundamentals, such as unpatched systems, insufficiently trained users, and unreviewed alerts.
Similarly, the escalation of wars or crises is often attributable to unexamined assumptions.
Both scenarios arise from neglecting the primary principle of tactical disposition: understanding one’s position before determining a course of action.
Modern Application
- In cybersecurity: organizations should implement defense-in-depth strategies, automate routine checks, and prioritize cultivating awareness rather than fear. Emphasizing culture over blame.
- In governance: it is essential to align objectives with available capacity, critically assess the true cost of each commitment, and recognize that restraint can be the most strategic option.
This parallel represents a recurring pattern rather than a mere metaphor.
Practitioner’s Questions To Ask Yourself:
- Am I defending by hope instead of design?
- Which tools add noise without adding clarity?
- What assumptions have gone unchallenged for too long?
- Where has “doing more” replaced “preparing better”?
Final Reflection
While invincibility is not the explicit objective, it is often the understated result of an effective security architecture. Complete protection cannot be guaranteed. However, it can be achieved through patience and persistence. Although this approach may lack glamour, in the ongoing struggle to maintain tactical disposition, it remains essential.
Sun Tzu’s good fighter was never reckless, never idle. He shaped his defenses so well that the enemy’s attacks lost meaning.
Nations and security architects should adopt similar practices. Consistently apply the principles of tactical disposition, exercise prudent stewardship of public resources, and cultivate strength, resilience, and wisdom.
The objective is not to engage in conflict frequently, but to do so only when absolutely necessary. Making it essential to fully understand and apply this story’s principles:
“The good fighters of old first put themselves beyond the possibility of defeat, and then waited for an opportunity of defeating the enemy.”
“Thus it is that in war the victorious strategist only seeks battle after the victory has been secured, whereas he who is destined to be defeated, first fights, and afterwards looks for victory.”
Hard Truths, Not Hashtags: 5 Nutrition Myths That Won’t Die
When you’ve trained on the mats, coached clients through cleans, kettlebell swings, and meal prep execution, and watched everyday athletes chase their performance goals, you start to see the myths vs reality.
The claims that sound sexy.
Some strategies seem fresh and innovative.
And there are promises that seem too good to be true and usually are.
Here are five of the most persistent nutrition myths that still persist in fitness culture to this day. These myths can hold back your progress, make your habits harder, and limit your performance.
Let’s put these myths to rest.

Myth 1: Carbs Make You Fat, So Avoid Them
The belief that carbohydrates are always “bad” is one of the oldest myths in fitness. Over time, people started to think of “carbs” as just donuts and soda, forgetting that fruits, vegetables, rice, and oats are also carbohydrates.
Carbohydrates are your body’s preferred fuel source for high-intensity movement. In sprinting, lifting, grappling, and EMOMs. When you cut carbs too aggressively, especially around training, you’re cutting the fuel that keeps the engine running and ready for its highest performance.
Of course, someone who doesn’t move much and eats 400 grams of sugary carbs every day will gain fat. But if you’re an athlete training 4 to 6 times a week and still avoiding fruit, you’re likely to struggle with recovery, mental clarity, and performance.
Carbs are not the problem. The real issues are poor timing, portion sizes, and choosing the wrong sources. It’s important to know the difference.
Myth 2: More Protein Equals More Muscle
It’s easy to think of protein as a magic solution for building muscle. But the idea that you can just drink more shakes and automatically grow isn’t true. Your body can only use a certain amount of protein at a time, and anything extra just adds calories.
If your training lacks volume, intensity, or progression, no amount of protein will magically build muscle. If your sleep is poor, your recovery window is compromised. And if your stress is off the charts, you’ll break down more than you build.
Think of protein as a critical piece of the puzzle, but not the only one. Focus on consistent daily intake (spread across meals), quality sources (whole food > processed powders), and real recovery habits. You don’t get stronger just by eating. You get stronger by absorbing nutrients after solid training and real rest.
Myth 3: Fat Slows You Down, Avoid It
Fat was blamed during the low-fat trends of the 1980s and 1990s, and some people still avoid it. Even now, many choose “fat-free” salad dressing and worry that eating an avocado will hurt their progress.
The truth is, healthy fats are needed for hormone production, joint health, cell repair, and brain function. Athletes who avoid fat for too long often have trouble sleeping, joint pain, low libido, or hormone problems.
You don’t have to add butter to your coffee or eat only bacon to benefit from fat. But if you’re training hard and still eating like it’s the 1990s, you’re missing out on better performance.
Balance your macronutrients to build a strong foundation.
Myth 4: You Shouldn’t Eat After 7 PM
This one sticks around like gym chalk on a black shirt. The belief is: eating late = fat gain. But what the science actually says is this: calorie balance, nutrient timing, and daily movement matter far more than the clock.
If you train in the evening, work a night shift, or just eat dinner late, you’re not hurting your progress. It’s your routine. The real problem is eating junk food late at night, snacking without thinking, stress-eating, or skipping meals earlier.
For athletes, skipping a meal after training just because it’s late can lead to poor recovery and insufficient sleep. Your body doesn’t track time; it just needs the right fuel.
Myth 5: Supplements Replace Meals
Supplements have become a billion-dollar industry promising shortcuts. But the truth? They’re called supplements for a reason. They supplement a well-rounded diet. They don’t replace one.
If your diet isn’t steady, you don’t drink enough water, and your sleep is poor, no supplement will fix your performance.
Whey protein is fine when you’re on the go. Electrolytes help when training volume is high. But if you’re leaning on powders, bars, or mystery potions more than you’re eating real food? You’re missing the point.
Eating real food leads to real results. Supplements are optional, but hard work, recovery, and whole foods are essential.
Bonus Myth That Needs to Be Busted Once and For All
You Need BCAAs to Build Muscle and Recover
Branched-chain amino acids (BCAAs) have been marketed like magic, drink this neon liquid, build more muscle, recover faster, dominate your workouts. But if you’re eating enough complete protein daily (think eggs, meat, fish, dairy, or quality whey), you’re already getting all the BCAAs your body needs.
The truth is, BCAAs are only three out of nine essential amino acids, and they don’t work alone. Building and repairing muscle needs all of them. Taking BCAAs instead of full protein is like bringing only a few bricks to a construction site and expecting to build a whole building.
This myth sticks around because supplement companies make a lot of money from BCAAs. They’re cheap to produce, easy to flavor, and simple to market to people who want quick fixes or think more is always better. Unless you train for hours without eating or have a very low protein diet, BCAAs aren’t necessary.
The bottom line: If you get enough protein each day, you don’t need BCAAs. Save your money and enjoy a good meal instead.
Why This Actually Matters
I’ve been in boardrooms, meal prep kitchens, and war rooms. I’ve been a fighter and sat across from fighters who measure life in rounds, and clients who measure progress in PRs.
The pattern is always the same:
Myths confuse, limit, and delay growth. But once you break your nutrition down into simple truths, reality & function over fad, you become harder to fool, harder to distract, harder to derail.
Field Notes: Your Mission This Week
• Pick one myth above you’re still believing. Write it down. Then spend 10 minutes challenging it with real information.
• Swap one habit: Still avoiding carbs around workouts? Try a simple “safe” carb on a heavy day. Watch how recovery and hunger change.
• Track one metric: Not the scale. Maybe energy, sleep, or workout quality. Let that be your barometer, not guilt.
• Talk it out: Share one busted myth with someone—client, teammate, or partner. Watch the shift when you trade confusion for clarity.
Nutrition is more than just eating. It’s about being ready for training, workouts, and daily life with the right fuel to help you succeed, not hold you back.
Security Without Pessimism: Shadow IT – When Convenience Becomes a Security Risk

The Shortcut That Became the Standard
We’ve all done it.
You’re trying to get something simple done, but the company’s “official” tool takes six steps and two approvals just to open a project. So, you find a better one, quicker, cleaner, easier.
Maybe it’s a shared Google Sheet, a new messaging app, or some AI productivity tool that actually works. It saves you time, gets results, and honestly, no one seems to mind.
That is, until someone finally notices.
That’s Shadow IT, the silent, well-intentioned workaround that slowly turns into a security liability.
The issue isn’t carelessness; it’s the drive for efficiency.
The Anatomy of Shadow IT and How It Slips Through
Shadow IT doesn’t begin as an act of rebellion. It starts as a way to get things done.
Teams feel pressure, tools are slow, and company processes can’t keep up. So, someone tries a new tool that bends the rules, just for this one time.
That quick fix gets shared with others and soon becomes the usual way of doing this.
Before long, company data is moving through several tools that no one has officially approved:
- Free cloud drives with no encryption.
- Personal accounts are used for client data.
- Messaging platforms without audit trails.
- Chrome extensions quietly sync user info to external servers.
It’s not done out of malice; it’s just human nature. People pick what helps them get the job done. But each time we choose convenience over control, we lose sight of what’s happening.
Why Good People Go Rogue
Most shadow IT isn’t about breaking rules. It’s about finding better ways to work.
People want to do their jobs well. When approved systems slow them down, they look for alternatives. This creativity isn’t careless, but it can still be risky.
Most people don’t focus on compliance when facing a tight deadline. They focus on getting results.
Here’s the problem: attackers know this. They rely on busy teams taking shortcuts, creating unmonitored accounts, or storing data in places that go unnoticed.
Shadow IT doesn’t look like rule-breaking. It looks like taking initiative.
When Visibility Vanishes
Each unapproved app creates another potential risk.
Security teams can’t track data, fix vulnerabilities, or control access. Soon, they may not even know what needs protection.
If something goes wrong, you can’t protect what you can’t see. A hacked third-party app or a compromised account can quietly put the whole system at risk.
Shadow IT isn’t a single big mistake. It’s many small, hidden problems. By the time someone notices, it’s often too late to trace the cause.
Balance Control with Capability
The solution isn’t to make things stricter. It’s to make official tools easier to use.
Security should support people in their actual work, not just follow what policy says.
Here’s what helps:
- Simplify the approved stack. If it’s painful to use, it’s already compromised.
- Create a “request to innovate” process. Let employees suggest tools safely.
- Shadow IT discovery audits. Not witch hunts — open conversations.
- Default to transparency. Make it normal to say, “I’m testing this app” without fear.
The aim is partnership, not strict control. If security punishes creativity, people will just hide what they’re doing. Problems will still find a way through.
Building Trust Around Tools
You can’t get rid of Shadow IT by being strict. The only way is to build trust instead of secrecy.
If people think speaking up will get them in trouble, they’ll stay silent. But if they see it as a chance to work together, you’ll know what’s really happening.
The best workplaces see curiosity as a strength, not a risk. Security and innovation aren’t enemies; they work together toward the same goal.
Final Thought
Shadow IT isn’t caused by bad people. It happens when good intentions don’t fit with strict systems. For security to keep up with creativity, it needs to act as a guide, not just a gatekeeper.
That’s not being pessimistic. That’s reality and an opportunity to get better, together.
The Art of Cyberwar | Part III | Attack by Stratagem
The principle:
If you know the enemy and know yourself, you need not fear the result of a hundred battles. Sun Tzu – Chapter III

Strategy vs. Stratagem
A strategy is designed for longevity, while a stratagem addresses immediate challenges. Strategy anticipates years ahead to foster resilience. Stratagem focuses on the next breach, exploit, or distraction.
Within cybersecurity, strategy encompasses architectural design, layered controls, validated incident response plans, and a culture prepared to act decisively during crises. Stratagem represents the attacker’s tools, such as persuasive emails, covert code injections, or precisely timed physical penetration tests.
Both approaches are powerful, yet each possesses inherent limitations.
The Modern Battlefield: Fluid and Fractured
The threat landscape evolves continuously. Traditional boundaries are replaced by cloud environments, API vulnerabilities, and interconnected third-party networks. Security architects must prioritize adaptability and fluidity over static defenses to effectively mitigate risks.
Zero Trust principles, continuous validation, and integrated security practices throughout the development lifecycle enable proactive identification and mitigation of vulnerabilities prior to production deployment. In an environment where compromise is presumed and rapid response is critical, these measures are indispensable.
Effective defenders adopt a proactive stance. They anticipate adversary actions, analyze behavioral patterns, and design systems to adapt under attack rather than fail.
Attack by Stratagem: The Psychology of Exploitation
Major breaches often originate through psychological manipulation rather than technical flaws. Techniques such as phishing, vishing, and deepfakes exploit cognitive vulnerabilities to diminish user awareness. This approach mirrors historical propaganda methods, where controlling perception leads to controlling behavior.
While governments previously leveraged headlines and radio broadcasts, contemporary attackers exploit digital interfaces such as login pages and hyperlinks. Both strategies depend on user fatigue, habitual behavior, and misplaced trust. If users believe a fraudulent login page is legitimate, they inadvertently compromise security.
Similarly, if citizens equate fear with patriotism, they may relinquish critical judgment in favor of perceived safety. As Ben Franklin observed, individuals who prioritize temporary safety over essential liberty may ultimately forfeit both: “Those who would give up essential Liberty, to purchase a little temporary Safety, deserve neither Liberty nor Safety.“
This tactic operates effectively across a spectrum, from individual email inboxes to broader ideological movements.
The Architecture of Awareness
A resilient security architecture reflects the characteristics of an aware and vigilant mindset.
Network segmentation limits the blast radius. Application hardening predicts misuse before it happens.
Firewalls and Security Information and Event Management (SIEM) systems provide the critical, irreplaceable resource of time.
Knowing your environment is knowing yourself.
Without a thorough understanding of all dependencies, exposures, and behavioral patterns, it is impossible to detect significant changes or anomalies. The same principle applies at the national level: when societies cease to critically evaluate their narratives, division and deception proliferate with ease.
Propaganda Built Into the Code

From Woodrow Wilson’s Committee on Public Information to the televised theater of Desert Storm, America learned how framing shapes belief.
Attackers apply similar principles, constructing their deceptive tactics by exploiting established trust.
Deceptive login pages replicate corporate portals, ransomware communications adopt professional language, and deepfakes are crafted to appear and sound authentic.
The primary threat is not the attack itself, but the absence of awareness regarding potential dangers. Stratagem prevails when critical scrutiny is abandoned.
Reverse Engineering the Present
Post-incident analyses consistently reveal that warning signals were present before breaches. Although alerts, logs, and telemetry data were available, they did not translate into actionable understanding.
Visibility does not equate to genuine situational awareness.
Historical events reinforce this observation.
The United States has engaged in conflicts based on incomplete or inaccurate information, often mistaking perception for certainty.
In both cybersecurity and geopolitics, failure frequently results from conflating raw data with meaningful insight.
Understanding adversaries requires effective intelligence gathering, including threat hunting, reconnaissance, and red-team exercises.
Self-awareness in cybersecurity necessitates discipline, such as maintaining asset visibility, ensuring policy integrity, and sustaining composure during operations.
A deficiency in either area enables adversarial stratagems to succeed.
The Quiet Defense
The most robust networks, analogous to resilient individuals, operate discreetly.
They do not engage in ostentatious displays; instead, they maintain a constant state of preparedness.
Their resilience is embedded within their structural design rather than expressed through rhetoric.
Authentic resilience does not stem from more active dashboards or faster technical tools. Resilience is rooted in organizational culture, situational awareness, and a humble approach. It is defined by the ability to learn, adapt, and respond more rapidly than emerging threats.
Cybersecurity, akin to statecraft, is a continuous endeavor to prevent breaches. Success is achieved not by engaging in every conflict, but by anticipating and neutralizing threats before they materialize, thereby securing victory without ever having to fight. Bringing us full circle back to understanding the fundamental nature of the original principle: If you know the enemy and know yourself, you need not fear the result of a hundred battles.
Top 1%…at something
Grammarly sent me a little “you might have a problem” email earlier this week.
Apparently, I’ve written over 900,000 words in the last five weeks. They claim it’s more than 99% of users, with more unique words than 99% of them too. I don’t know how that’s true, but I definitely have been writing a lot lately. I had no idea it was even close to that much.
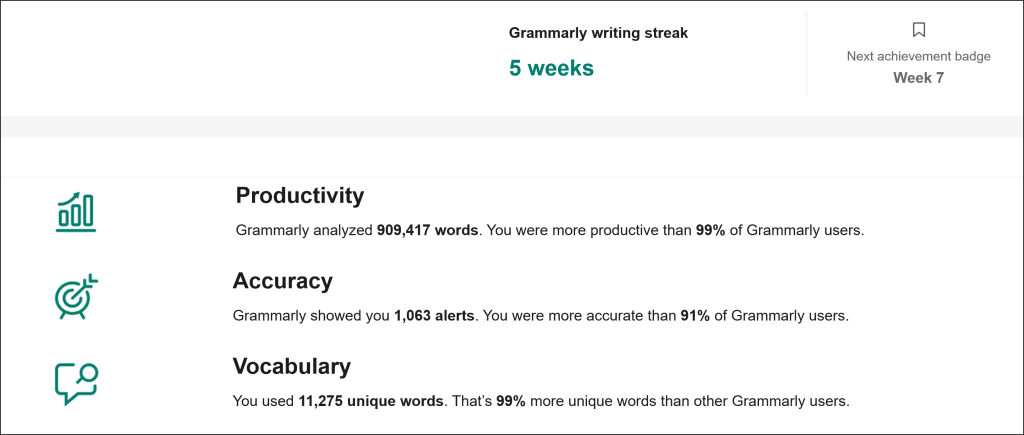
It’s both kind of cool and kind of hilarious. Why? Because it wasn’t part of a strategy, a streak, or even a goal. It just came from putting in the writing reps. One sentence, one section, and one page at a time.
I’d love to say it’s all poetry and brilliance. But it’s hardly that. It’s been mostly retelling of long hours coaching, martial and security strategies and the kind of sentences that get rewritten three or four times before they sound right.
Still, I’ll take it.
Some of it’s for the book. Some of its old stories I’m finally writing down. Some of it’s heart-wrenching, some of it’s about training, traveling, coaching, fighting, or just trying to make sense of the thoughts that appear between deadlifts, dog walks, deep in the mountains or just walking into the office.
It reminded me of something George Washington once said:
“To be prepared for war is one of the most effective means of preserving peace.”
Sometimes the work is the preparation. And sometimes the work is the peace. Not trying to be prolific, just consistent.
Keeping the standard high, even when no one’s watching.
So, here’s to showing up, stringing some stories together, and hoping at least a few of them land where they’re supposed to.
Now, back to work.