History shows that the biggest threats to national security, safety, and sovereignty usually come from within. Empires, and leaders, often fail not because they are weak, but because they try to do too much, too quickly, and often end up heading in the wrong direction.
The Yalta Conference in February 1945 brought together Churchill, Roosevelt, and Stalin in an alliance of necessity. Few in the 1930s could have imagined democratic America and Britain siding with Stalin’s Soviet Union; yet necessity led to a partnership with lasting consequences.
The alliance beat Nazi Germany, but it also allowed the Soviet Union to spread into Eastern Europe, which led to the Cold War. The key takeaway: short-term use of power without considering long-term impact can resolve immediate issues but create new, lasting problems.
The same risks are present in cloud security today. Trying to do too much still undermines resilience.
Why Overreach Happens
Overreach is a common trap. If having some power is good, it’s easy to think that having more is better. In cybersecurity, this often happens because of:
- Fear of falling behind leads teams to adopt new tools without a clear strategy.
- Vendor pressure, with marketing insisting, “If you don’t have this, you’re insecure.”
- Internal signaling, where having numerous tools initially appears impressive, but problems soon emerge.
Historical Lessons: The Cost of Overreach
Germany in WWII: Too Much, Too Fast
Germany under Hitler is a classic example of overreach. In 1941, the Nazis invaded the Soviet Union. Initially, their advance was rapid, and they gained significant territory. However, German forces became overstretched, supplies dwindled, winter conditions set in, and the supply lines became unmanageable. What appeared to be a demonstration of power ultimately contributed to their downfall.
Lesson: Expansion without capacity undermines itself.
Japan: Provoking Too Many Enemies
Japan’s decision to attack Pearl Harbor in 1941 reflected a similar flaw. In pursuit of empire across Asia, Japan provoked a much larger adversary: the United States. Instead of consolidating its position, this overreach led to a conflict Japan could not sustain. Lesson: Overreaching creates adversaries you can’t manage.
The Allies: Yalta’s Unintended Consequences
Even the victors faced challenges. The Yalta alliance was necessary at the time, but also carried significant risk. By permitting the Soviet Union to expand into Eastern Europe, the Allies set the stage for forty years of Cold War tension, arms races, and indirect conflicts. Gaining power in one region led to new risks elsewhere.
Lesson: Gains made without foresight can create future vulnerabilities.
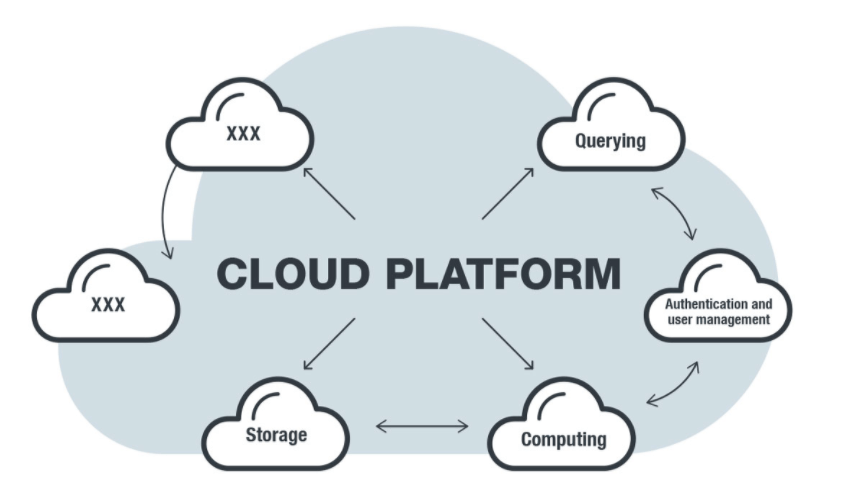
The Cost of Overreach in Cloud Security
The same dynamics play out in modern cybersecurity:
- Integration gaps: When you have too many tools, it’s like an army spread too thin—there are weak spots attackers can find.
- Alert fatigue: More dashboards overwhelm teams, dulling response rather than sharpening it.
- Diluted focus: Chasing new tools causes basics (IAM, logging, patching) to be neglected.
The main takeaway is that the paradox is that spending more and adding complexity often reduces resilience rather than strengthening it.
The Better Path: Discipline and Restraint
History points to a better approach. Resilience isn’t about growing without limits. It comes from balance, self-control, and getting the basics right.
For nations, that means understanding the limits of alliances and occupations. For cloud teams, it means:
- Focusing on fewer, stronger tools that integrate smoothly.
- Start by mastering the basics: IAM policies, patching cycles, logging, and monitoring. These may not be exciting, but they are essential.
- Resisting the urge to sprawl. Don’t buy tools or add features for the sake of appearances. Invest only where it truly adds resilience.
Closing Parallel
Yalta reminds us that even the strongest powers can make bargains that carry unintended consequences. Overreach may appear to be a sign of strength in the moment, but it often sows the seeds of weakness for the future.
In cloud security, the same is true. More tools don’t equal more safety. Complexity can backfire. Overreach creates vulnerabilities. The key lesson: resilience means mastering the essentials and exercising discipline, not doing more for the sake of it. This is as true in geopolitics as it is in cybersecurity.
Where have you seen overreach undermine resilience in your organization?
Want to dive deeper into the history and strategy behind these lessons? Here are some recommended reads:
- The Origins of The Second World War, by A.J.P. Taylor
- Depression, War, and Cold War: Studies in Political Economy, by Robert Higgs
- Churchill, Hitler, and “The Unnecessary War”: How Britain Lost Its Empire and the West Lost the World, by Patrick J. Buchanan
- The New Dealers’ War: Franklin D. Roosevelt and the War Within World War II, by Thomas Fleming
- The War That Ended Peace: The Road to 1914, by Margaret MacMillan
- Paris 1919: Six Months That Changed the World, by Margaret MacMillan