1. Implement Strong Access Controls
- Role-Based Access Control (RBAC): Ensure that only authorized personnel have access to sensitive data. Assign permissions based on roles and responsibilities.
- Multi-Factor Authentication (MFA): Require MFA for accessing sensitive systems and data to add an extra layer of security.
2. Regular Security Training and Awareness
- Staff Training: Conduct regular cybersecurity training sessions for teachers, administrators, and support staff to recognize phishing attempts, social engineering, and other common threats.
- Student Awareness: Educate students about safe online behaviors, the importance of password security, and how to avoid suspicious links and downloads.

3. Use Strong Password Policies
- Complex Passwords: Enforce the use of strong, complex passwords that include a mix of letters, numbers, and special characters.
- Password Management: Encourage the use of password managers to help staff and students manage their passwords securely.
4. Network Security
- Firewalls: Deploy firewalls to protect the school’s network from unauthorized access and malicious traffic.
- Intrusion Detection and Prevention Systems (IDPS): Implement IDPS to monitor and respond to potential threats in real time.
- Segmentation: Segment the network to limit access to sensitive data and reduce the attack surface.
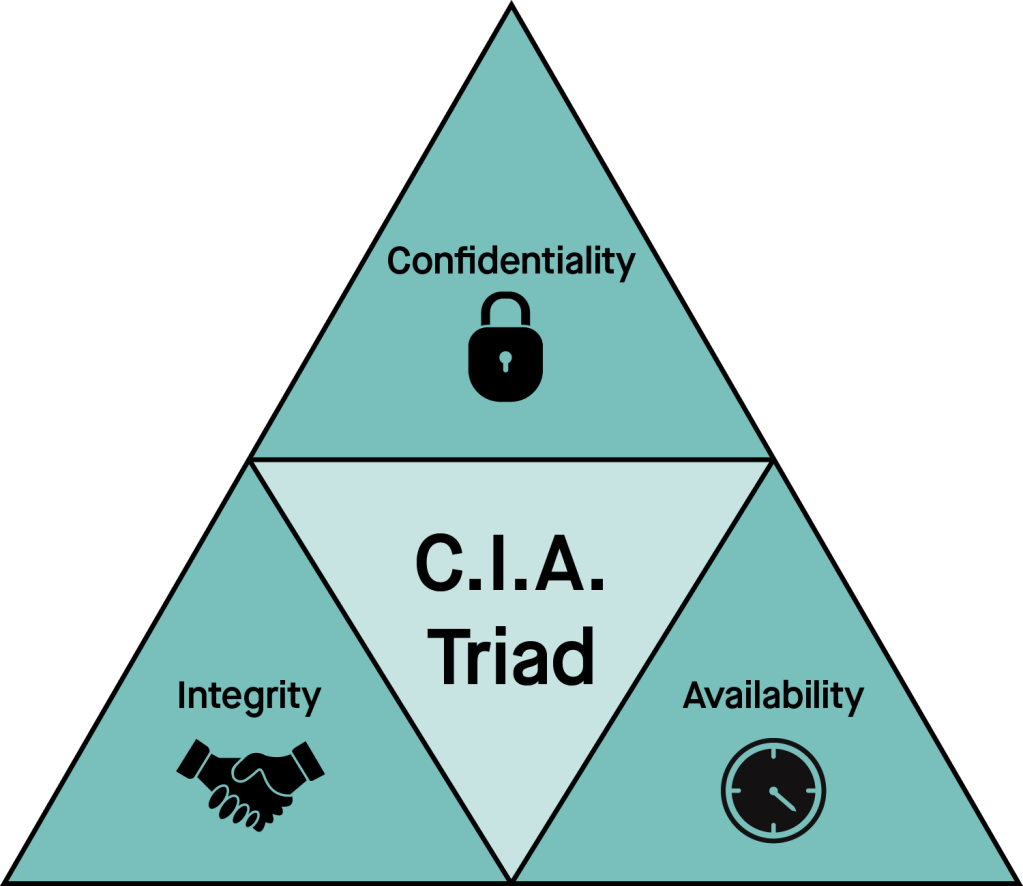
5. Data Encryption
- Encryption at Rest and in Transit: Ensure that all sensitive data is encrypted both when stored and when transmitted over the network.
- Secure Communication Channels: Use secure protocols like HTTPS, SSL/TLS, and VPNs for remote access and data transfer.
6. Regular Updates and Patch Management
- Software Updates: Keep all software, including operating systems, applications, and security tools, up to date with the latest patches and security fixes.
- Automated Patch Management: Use automated tools to manage and apply patches consistently and promptly.
7. Regular Backups and Disaster Recovery Planning
- Data Backups: Perform regular backups of critical data and store them securely offsite or in the cloud.
- Disaster Recovery Plan: Develop and regularly test a disaster recovery plan to ensure quick recovery from data breaches, ransomware attacks, or other disruptions.

8. Endpoint Security
- Antivirus and Anti-Malware: Install and maintain up-to-date antivirus and anti-malware solutions on all devices.
- Mobile Device Management (MDM): Use MDM solutions to manage and secure mobile devices used by students and staff.
9. Application Security
- Secure Software Development: Ensure that applications developed or used by the school follow secure coding practices and are regularly tested for vulnerabilities.
- Third-Party Applications: Vet and monitor third-party applications for security compliance before integrating them into the school’s IT environment.
10. Physical Security
- Secure Access to Facilities: Implement physical security controls like locks, access badges, and surveillance cameras to protect areas where sensitive data is stored.
- Device Management: Ensure that devices such as laptops, tablets, and USB drives are securely stored and tracked.

11. Incident Response and Management
- Incident Response Plan: Develop and maintain a comprehensive incident response plan outlining steps to take in the event of a data breach or security incident.
- Regular Drills: Conduct regular incident response drills to ensure that staff are prepared to handle security incidents effectively.
12. Compliance and Auditing
- Regulatory Compliance: Ensure compliance with relevant regulations such as FERPA (Family Educational Rights and Privacy Act) and COPPA (Children’s Online Privacy Protection Act).
- Regular Audits: Conduct regular security audits and assessments to identify and address vulnerabilities and ensure ongoing compliance with security policies.