Most workouts have a loophole. If you know how to do them, you can kip and be done in less than a minute. Most dudes who do “pull-ups” cheat the range of motion like it’s a professional sport by never fully extending at the bottom, and/OR do NOT get their chins over the bar. But, every now and then, rules will strip everything away and reveal the raw truth.
That’s the point of this challenge: 30 strict pull-ups for time.
The rules are simple but tough:
- Must be done in sets of 5 or 10 only. No singles, no doubles, and no kipping (this time).
- NO half a$$ Pete Hegseth or RKF, Jr. reps.
- Full extension at the bottom. Elbows locked out every time.
- Chin over the bar at the top. No “almost” reps. No, “I was so close that time.”
- Discipline over ego.
My time? Watch and see.
But the question you might be asking is, “Why Does This Even Matter?”
This is more than a physical test; it’s a mindset test, like the pressure faced in cybersecurity, leadership, or life.
Here’s what the workout teaches:
- Constraints Make You Stronger
Without the rule of “5 or more reps per set,” you’d see people game the system: 30 singles, done easily, no challenge. But rules force focus. They push you past your comfort zone and into real growth.
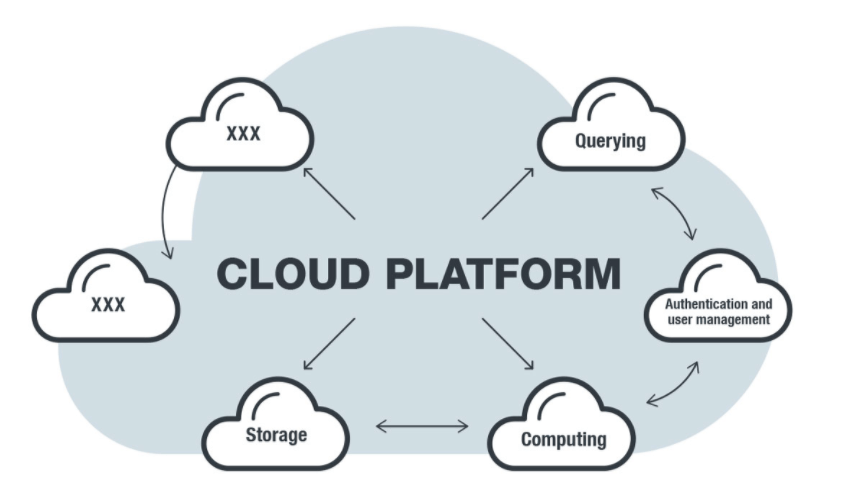
Cloud security works on the same principle as the pull-up challenge: doing things the hard, correct way leads to lasting results. In cloud security, if you make permissions too loose or skip essential controls, it seems easier—just like doing easier pull-ups. But real security comes from applying restrictions such as least privilege, multi-factor authentication, and segmentation. These are to security what strict form is to strength: they are challenging but essential for durability.
2. Form Is Discipline
Locking out every rep is about integrity. Cutting corners in training leads to cutting corners under stress.
Cyber pros know the drill: if you skip patch cycles, code reviews, or alerts, you won’t suddenly excel in a crisis—you will perform only as well as your training prepared you. The point is: in emergencies, people don’t ‘rise to the occasion’; they revert to their standard preparedness.
3. Speed Comes From Structure
Strict pull-ups in just over 2 minutes require planning: strict adherence to set sizes, rest, and when to push or hold back.
Incident response follows the same principle: structured speed is essential. Success comes from following practiced processes, not from last-minute effort.
4. Resilience Beats Flash
Nobody remembers the person who did 20 kipping pull-ups that looked good on Instagram but didn’t count in this instance. The athletes who succeed in the gym or in life are those who can perform strict reps under pressure, year after year.
Resilience isn’t glamorous. It’s strict adherence to form and standards. Reps stacked and basics drilled.
Closing Thoughts
Thirty strict pull-ups for time really isn’t about the number. It’s about the mindset: constraints, no ego, and the discipline not to go again sooner than you can complete at least another set of 5, along with persistence under pressure.
The lessons extend beyond workouts. Whether you’re securing cloud environments, writing policies, or leading teams, following real constraints, practicing discipline, and building resilience are as vital as adhering to strict form in your pull-ups when required.
Constraints can make you sharper. Discipline makes you stronger. Resilience makes you unbreakable.